Ars Technica old in malware campaign with never-forward of-viewed obfuscation
WHEN USERS ATTACK —
Vimeo also old by legitimate user who posted booby-trapped whisper material.

Getty Photos
Ars Technica modified into as soon as not too long in the past old to benefit 2nd-stage malware in a campaign that old a never-forward of-viewed assault chain to cleverly quilt its tracks, researchers from security company Mandiant reported Tuesday.
A benign image of a pizza modified into as soon as uploaded to a third-occasion net page and modified into as soon as then linked with a URL pasted into the “about” page of a registered Ars user. Buried in that URL modified into as soon as a string of characters that regarded as if it could perchance be random—however were truly a payload. The campaign also centered the video-sharing station Vimeo, where a benign video modified into as soon as uploaded and a malicious string modified into as soon as incorporated in the video description. The string modified into as soon as generated utilizing a scheme is known as Irascible 64 encoding. Irascible 64 converts text valid into a printable ASCII string format to inform binary recordsdata. Gadgets already infected with the foremost-stage malware old in the campaign mechanically retrieved these strings and fix in the 2nd stage.
Now not in general viewed
“That is a assorted and new plot we’re seeing abuse that can even be slightly appealing to detect,” Mandiant researcher Yash Gupta acknowledged in an interview. “That is one thing in malware we contain not in general viewed. It’s slightly attention-grabbing for us and one thing we wished to call out.”
The image posted on Ars looked in the about profile of a user who created an checklist on November 23. An Ars e book acknowledged the photograph, exhibiting a pizza and captioned “I love pizza,” modified into as soon as removed by Ars workers on December 16 after being tipped off by electronic mail from an unknown occasion. The Ars profile old an embedded URL that pointed to the image, which modified into as soon as mechanically populated into the about page. The malicious listless 64 encoding looked at the moment following the legitimate share of the URL. The string didn’t generate any errors or prevent the page from loading.
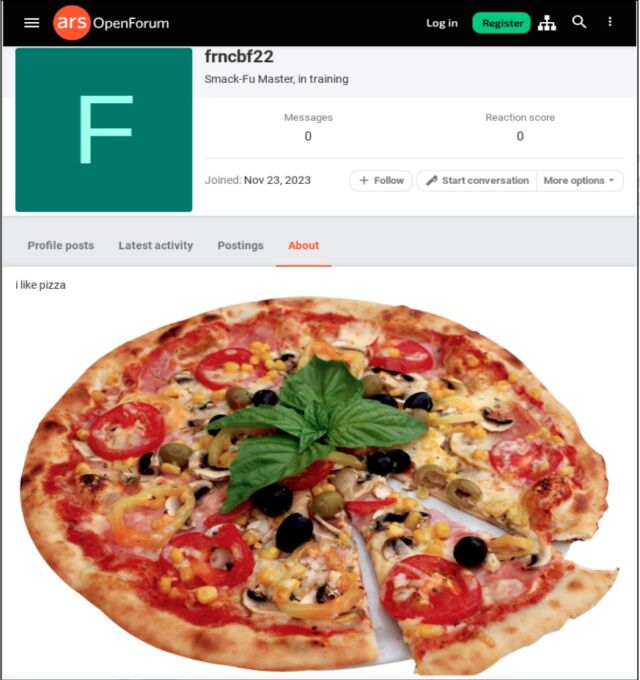
Lengthen / Pizza image posted by user.
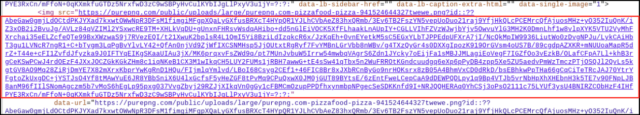
Lengthen / Malicious string in URL.
Mandiant researchers acknowledged there were no consequences for those that can contain viewed the image, either as displayed on the Ars page or on the net page that hosted it. It’s also not definite that any Ars users visited the about page.
Gadgets that were infected by the foremost stage mechanically accessed the malicious string on the stay of the URL. From there, they were infected with a 2nd stage.
The video on Vimeo labored equally, with the exception of that the string modified into as soon as incorporated in the video description.
Ars representatives had nothing extra to add. Vimeo representatives didn’t at the moment reply to an electronic mail.
The campaign got here from a risk actor Mandiant tracks as UNC4990, which has been packed with life since on the least 2020 and bears the hallmarks of being motivated by monetary manufacture. The crew has already old a separate new technique to waft below the radar. That scheme unfold the 2nd stage utilizing a text file that browsers and accepted text editors confirmed to be blank.
Opening the same file in a hex editor—a instrument for examining and forensically investigating binary files—confirmed that a aggregate of tabs, areas, and unusual traces were arranged in a scheme that encoded executable code. Admire the scheme animated Ars and Vimeo, utilizing this form of file is one thing the Mandiant researchers had never viewed forward of. Previously, UNC4990 old GitHub and GitLab.
The preliminary stage of the malware modified into as soon as transmitted by infected USB drives. The drives attach in a payload Mandiant has dubbed explorerps1. Infected devices then mechanically reached out to either the malicious text file or else to the URL posted on Ars or the video posted to Vimeo. The listless 64 strings in the image URL or video description, in turn, introduced about the malware to contact a station cyber net net hosting the 2nd stage. The 2nd stage of the malware, tracked as Emptyspace, continuously polled a expose-and-control server that, when instructed, would fetch and assign a third stage.
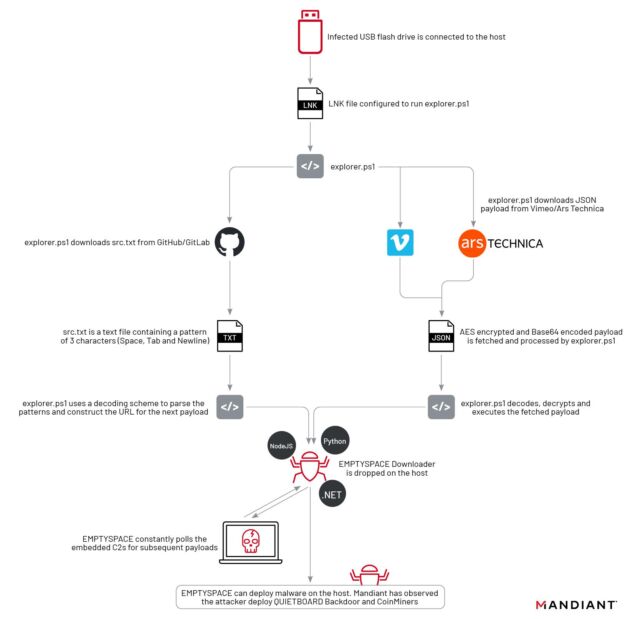
Mandiant
Mandiant has noticed the installation of this third stage in handiest one case. This malware acts as a backdoor the researchers song as Quietboard. The backdoor, in that case, went on to install a cryptocurrency miner.
Someone who’s concerned they might per chance were infected by any of the malware covered by Mandiant can check the indications of compromise half in Tuesday’s publish.




