How to grab if a USB cable is hiding malicious hacker hardware
We put a query to USB-C cables to fabricate a particular activity: transferring either files or files between devices. We give runt extra belief to the matter, nonetheless malicious USB-C cables can attain grand extra than what we put a query to.
These cables veil malicious hardware that may perchance well well intercept files, hear in on cell phone calls and messages, or, within the worst cases, spend full adjust of your PC or cell phone. The predominant of these looked in 2008, nonetheless support then they were very uncommon and pricey — which meant the everyday individual became as soon as largely safeguarded.
Since then, their availability has increased 100-fold and now with each and every specialist witness outlets selling them as “witness cables” to boot to unscrupulous sellers passing them off as legitimate merchandise, it’s all too easy to take one by likelihood and produce together hacked. So, how attain you know if your USB-C cable is malicious?
Extra reading: We tested 43 mature USB-C to USB-A cables. 1 became as soon as gigantic. 10 were uncertain
Figuring out malicious USB-C cables
Figuring out malicious USB-C cables isn’t any easy activity since they are designed to be conscious staunch like traditional cables. Scanning tactics were largely regarded as as essentially the most easy formulation to type the wheat from the chaff, which is what industrial scanning firm, Lumafield of the Lumafield Neptune industrial scanner reputation, no longer too lengthy ago put of living out to display.
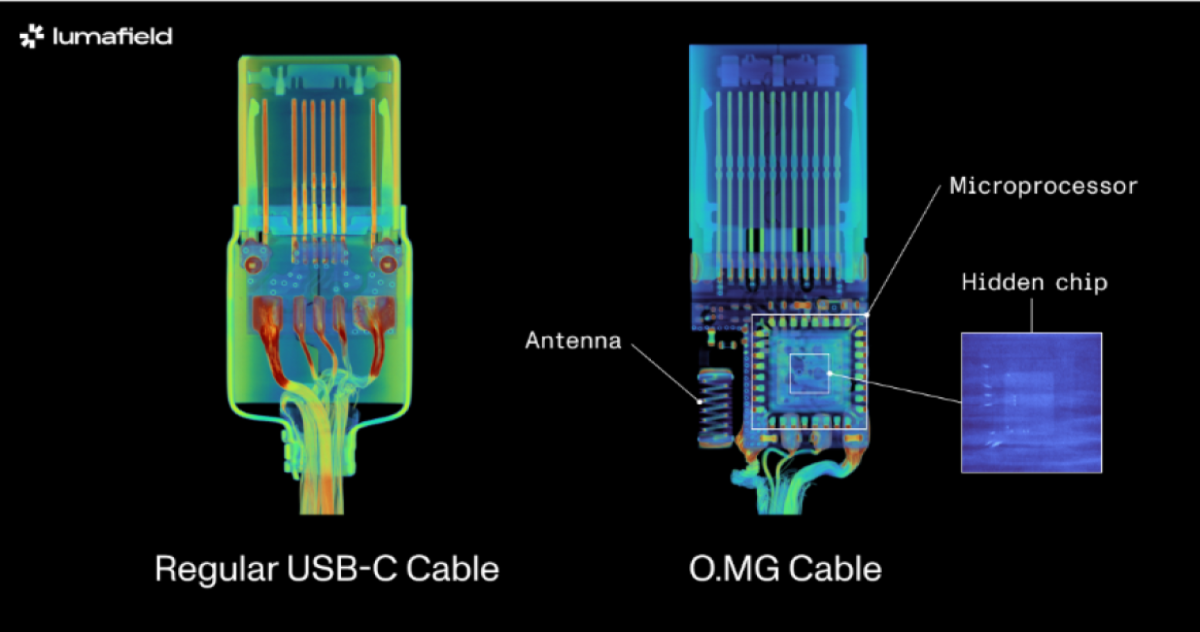
The firm employed each and every 2D and 3D scanning tactics on the O.MG USB-C cable — a successfully-identified hacked cable constructed for covert field-spend and compare. It hides an embedded Wi-Fi server and a keylogger in its USB connector. PCWorld Govt Editor Gordon Ung coated it support in 2021, and it sounds provoking as hell.
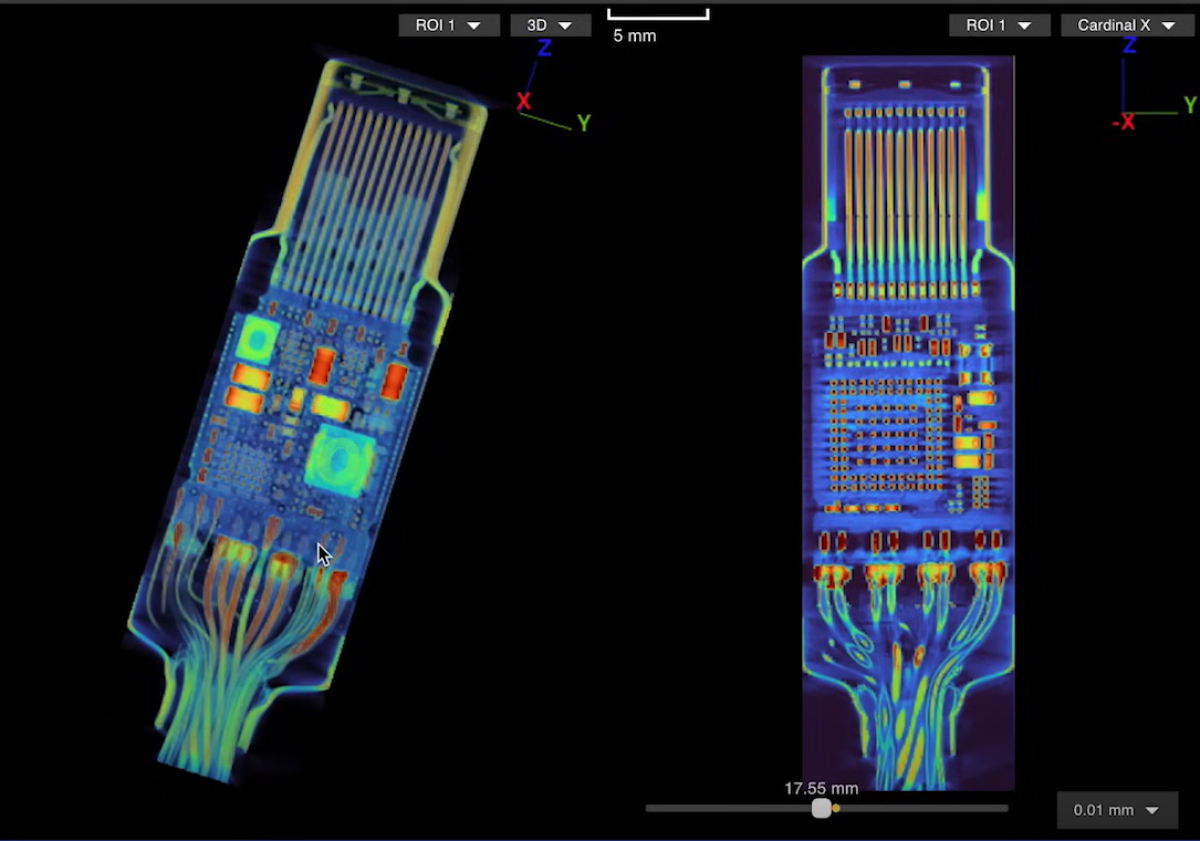
What Lumafield chanced on is attention-grabbing to bid the least. A 2D X-ray picture may perchance well well well title the cable’s antenna and microcontroller, nonetheless easiest the 3D CT scan may perchance well well well present off every other band of wires linked to a die stacked on prime of the cable’s microcontroller. You may perchance well well well presumably explore a 3D mannequin of the scan your self on Lumafield’s online online page.
The malicious hardware became as soon as visible with a 3D CT scan.
Lumafield
It confirms the worst — that that you just may perchance well be in a space to easiest unequivocally verify that a USB-C cable harbors malicious hardware with a 3D CT scanner, which unless you’re a medical radiographer or 3D industrial scientist goes to be inconceivable for you to attain. That being so, listed below are some tricks to dwell far from and title suspicious USB-C cables without high-tech gear:
- Steal from an very ideal vendor: Need to you don’t know and belief the heed, merely don’t take. Producers like Anker, Apple, Belkin, and Ugreen agree with rigorous quality-adjust processes that quit malicious hardware parts from making it into cables. Pointless to bid, the diversified reason is merely that you just’ll bring together an even bigger product — 3D scans agree with similarly printed how much less legitimate brands can lack traditional USB-C componentry, which is in a space to manual to immoral performance. Need to you’re within the market for a recent cable ethical now, watch our prime picks for USB-C cables.
- Look the warning signs: Look heed names or logos that don’t watch ethical. Irregular markings, cords which would be inconsistent lengths or widths, and USB-C connectors with heat emanating from them when no longer plugged in can all be giveaways that a USB-C cable is malicious.
- Employ the O.MG malicious cable detector: This detector by O.MG claims to detect all malicious USB cables.
- Employ files blockers: Need to you’re staunch charging and no longer transferring files, a blocker will be sure no files is extracted. Other than detecting malicious USB-C cables, the O.MG malicious cable detector functions as this type of files blocker.
- Employ a detection service: Need to you’re coping with extraordinarily subtle files for a commerce or governmental group, it is truly helpful to exhaust the services and products of a firm like Lumafield to detect malicious cables with 100 percent accuracy. This type of service will approach with a price, nonetheless it indubitably will be a small designate to pay for safety and peace of suggestions.
If this text has been an be conscious-opener relating to the dodgy tactics hackers exhaust to prefer your files, you’re no longer on my own. Malicious USB-C cables are silent no longer broadly identified about. That being so, be obvious to portion the pointers above with your loved ones and pals. The extra these that spend time to safeguard their files, the safer we are in a position to all be within the destroy.
Extra reading: Shopping a USB-C cable? 6 gotchas to gape out for
Author: Dominic Bayley, Australian Editor, PCWorld
Basically based mostly in Australia, Dominic Bayley is a hardcore tech enthusiast. His PCWorld center of attention is on PC gaming hardware: laptops, mice, headsets and keyboards.